A well-known inconvenience in the IT world is how the term “phishing” is pronounced the same way as “fishing”. This sometimes creates confusion—just like a real phishing attack! The Safe Surfer team has detailed several suggestions below that can help protect you from cybercriminals.
Hover first, click later
Attackers sometimes abuse hyperlinks (that is, highlighted web links on websites and emails) to make it appear that you’re going to a friendly site, when you’re really being led to a spoof site—a fake.
Pictured below is an example of what a crafted phishing attack (designed to steal bank account credentials) could look like in directing someone to a malicious site. See if you can spot the three phishing-related (that is, targeted) keywords designed to generate an image of plausibility surrounding the legitimacy of the email:
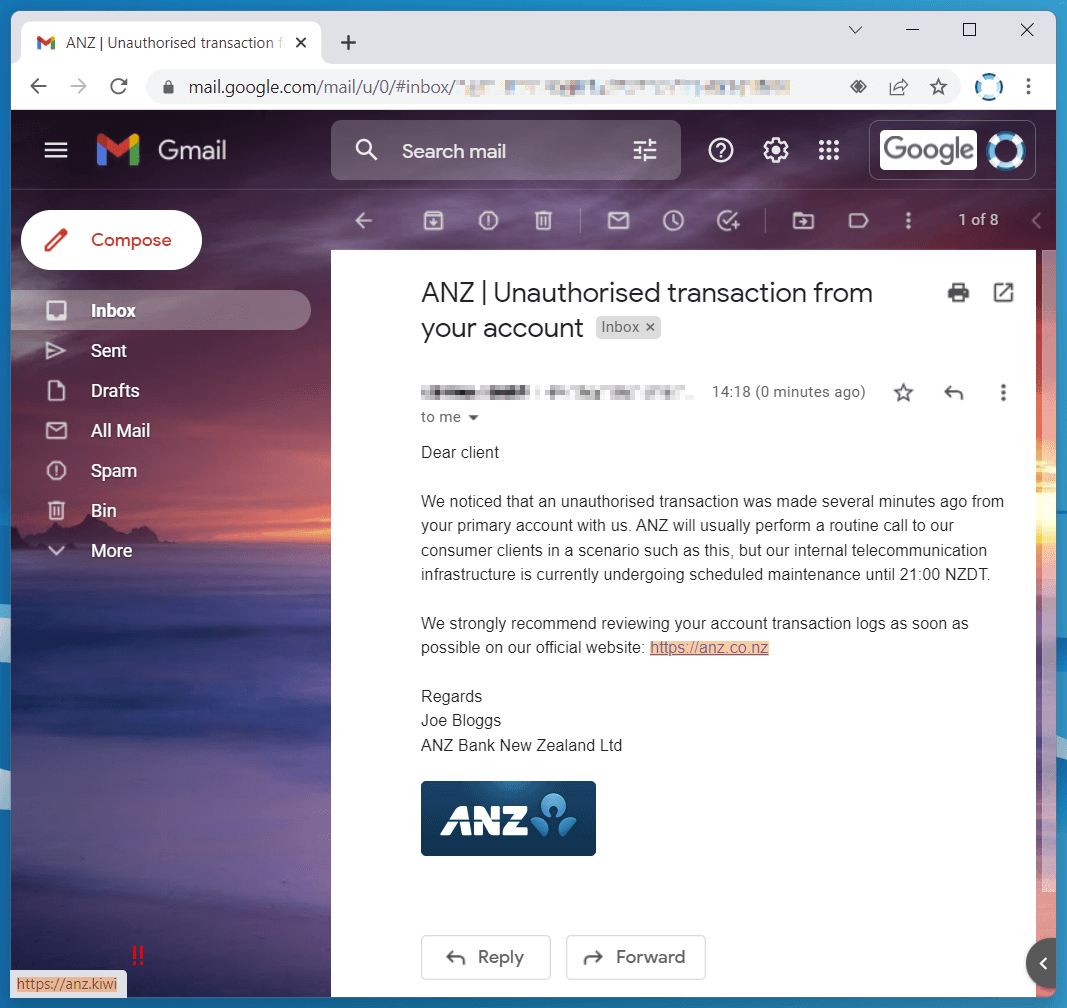
Notice how my hovering over the link in the email has shown inside the status bar (found at the bottom-left corner of the browser window) the actual destination if I click. As pictured, a bogus domain has been used to make the site look at least somewhat legitimate if caught by a glance.
The three phishing keywords are the following:
- The name of the real legitimate organisation (“ANZ”)
- The term “consumer clients”
- The local timezone (which is even in the right format for the time of year!), being “NZDT”
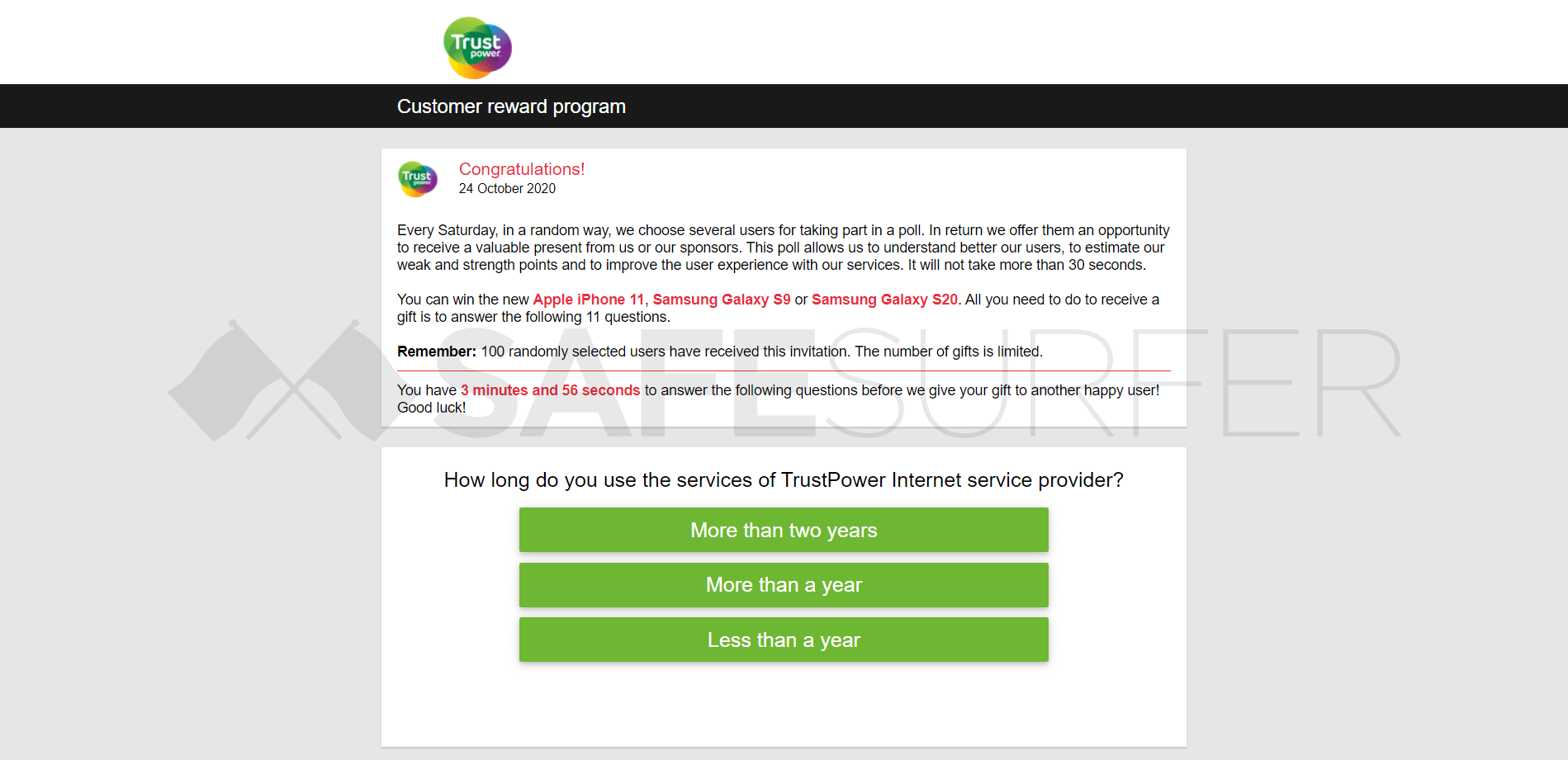
Pictured below is an real example of a phishing attack. This website’s system determines the ISP (Internet Service Provider) of the page viewer and changes the logo accordingly. The purpose of this attack is to derive personal information from you. This information could be used to steal finances or spam your email.
Pictured below is another real example of a phishing attack. This is an email caught by a spam filter (which has also neutralised a malicious hyperlink in the body of the correspondence). The purpose of this attack is to derive personal information from you to steal finances.
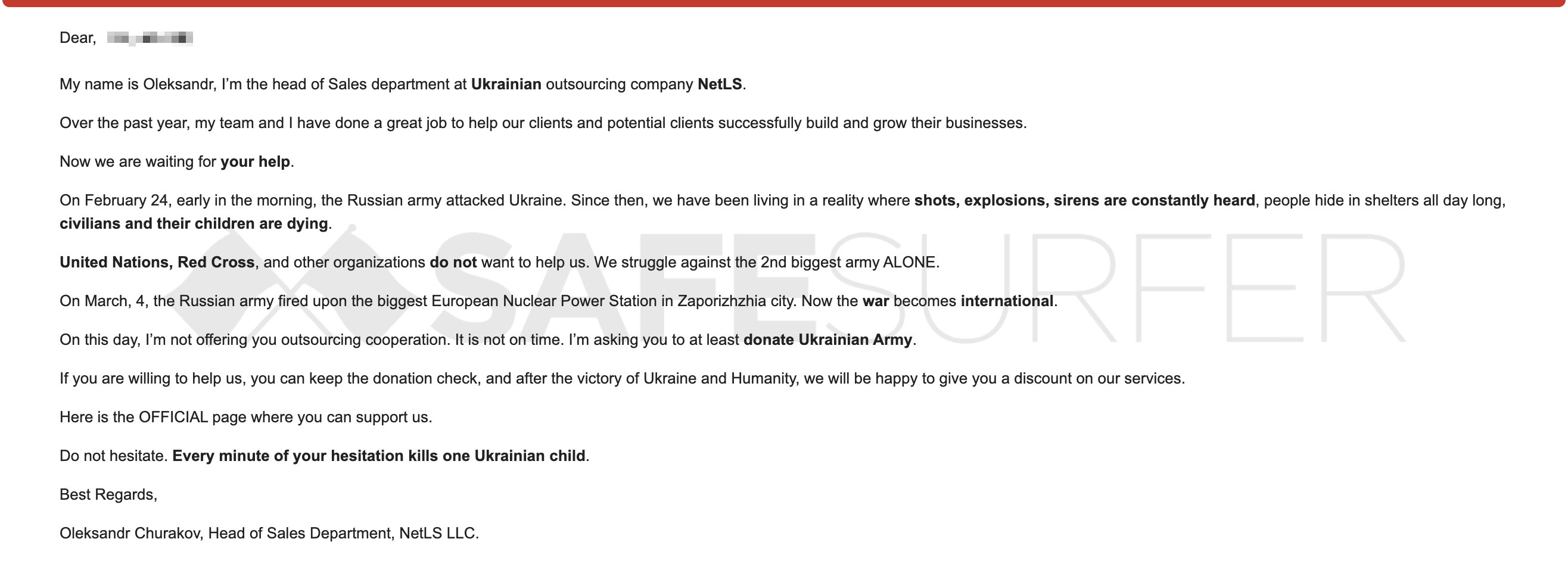
Attackers will often try to determine a service you may use, sometimes with even a sheer guess. Another commonly used method is to scare you into thinking that they have caught you doing something embarrasing, such as looking at pornography, and then threaten to send incriminating evidence to your device contact list if a ransom in Bitcoin is not paid. The “proof” of this discovery by the malicious actor is suggested by means of “undetectable low-level malware”. Bitcoin is technically an anonymous cryptocurrency when used, which makes it virtually untracable by nature. This makes it a highly popular method of transferring finances when cybercriminals attempt extortion. Perhaps the malicious actor never noticed the presence of Safe Surfer, which blocks pornography (for free!).
The key to staying safe is to make a habit of checking the sender’s email address and the destination of any hyperlinks. Ask yourself the following questions:
- Does this email come from a web domain I’m familiar with?
- If I go to click a hyperlink, will this take me to a legitimate site?
You should also avoid clicking shorten.ed/l1nk5. Sometimes legitimate web address shortening services (known as “URL shorteners”) are abused to hide the identity of the destination you will be sent to.
Check the padlock
An easy way for cybercriminals to sniff (that is, read) credentials is to intercept them as plain text. This could happen if the connection between you and a website is unencrypted. You can find the connection status information from the padlock icon on your web browser’s URL (web address) bar. Here are a couple of examples from common web browsers.
This is what an unencrypted connection looks like on Firefox. The padlock has a diagonal red line over it. This signifies an unencrypted connection. The padlock would otherwise be plain (to signify an encrypted connection).
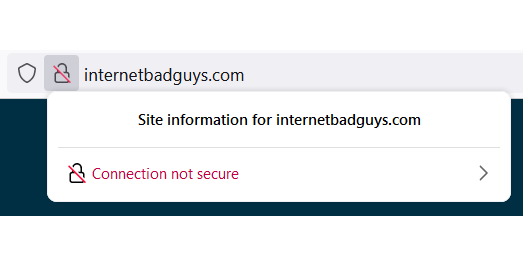
This is what an unencrypted connection looks like on Google Chrome. Instead of padlock, a warning sign accompanied by the text “Not secure” is shown. This message would otherwise be replaced with a plain padlock (to signify an encrypted connection).
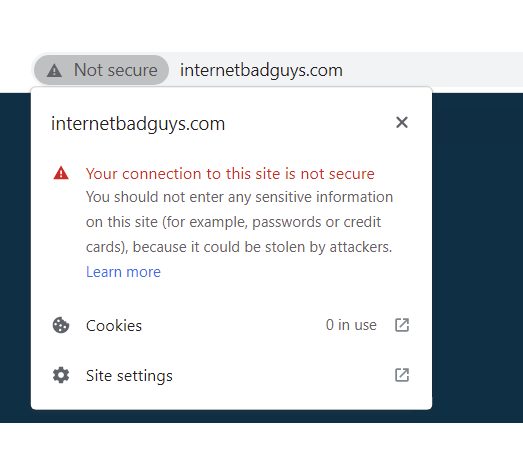
Pro tip: the presence of a padlock icon doesn’t necessarily mean that the site in question has a reputation for being safe. Rather, it signifies that the connection is encrypted. It’s also important to understand that a connection being unencrypted (such as when configuring a router on a local area network) doesn’t make it inherently unsafe to use.
Double-check the platform
Safe Surfer expects a rise in cyberattack scams given the current crisis in Ukraine as of posting this article. If you donate to help with humanitarian relief efforts, ensure that the organisation is reputable and the website you use is not spoofed from the original. This is a good habit to get into when sending money online, no matter what the site.
Get your devices protected with Safe Surfer
You don’t have to avoid attacks alone. We have designed Safe Surfer to update our phishing domain database every week with new malicious websites as they become known. We provide this blocking by default to our non-commercial users for free. We also provide a lot of other categories for blocking with a Pro Surfer subscription, such as uncategorised Russian (.ru) domains. Visit https://my.safesurfer.io/create-account and get your devices protected today with a 7-day free trial of premium features.
Header photo by Erik Mclean on Unsplash

